Authorise External Applications for a Short-Time Period
Imagine that your company is developing a new application that you will launch for a car manufacturer's infotainment system. The application offers a subscription service for accessing audio books and is currently available on web and smartphone platforms. Your objective is to integrate the new application with the existing IT infrastructure, which involves repurposing API endpoints.
Your business owners have secured a deal to deploy the application in a fleet belonging to a major rental company. Subsequently, the product team has identified that rental vehicles frequently have a high turnover of drivers, thus necessitating the need for this challenge to be addressed. There is pressure from both business owners and customers for the vehicle application to be user-friendly, while also integrating security by design. Should it prove necessary, the product team will strive to achieve a suitable balance between these two objectives.
The Most Convenient Implementation
Your IT infrastructure already has an identity provider (IdP) in place. Your APIs necessitate a valid access token for usage, which can be obtained from the IdP to allow authenticated user access.
The IdP is currently utilised by the website and the smartphone app. Therefore, it is proposed to leverage this workflow to authenticate users on your car's application, resulting in a seamless experience. The benefit is that users only need to know their login details and input them. Moreover, developers and operation engineers possess considerable implementation know-how for this option. Nevertheless, there are some disadvantages. Users must enter their login details, specifically, their usernames and passwords, via an infotainment interface, which can be somewhat inconvenient. Additionally, long-term security considerations must be taken into account for such a login. In a car rental scenario, it is important to prevent the next renter from accessing the previous renter's account. Therefore, when the car is parked and the ignition is off, access to the application should be revoked. However, this requires the user of your application to enter their full credentials each time, which can be cumbersome.
To address this issue, consider integrating a checkbox that keeps the login active even if the ignition is turned off. However, it is possible that some renters may neglect logging out before returning the car, resulting in a risk of unauthorised access by subsequent renters. To address this issue, a solution could be implemented by allowing someone to revoke all sessions, which would require a new login. However, users must still be aware that they have logged in and forgot to logout.
However, business owners do not believe this measure will achieve their goal of good security.
Authorising the Application in the Car
Consequently, an alternative method must be sought. A superior approach would be to grant the car's application an access token upon request. Although this may seem slightly convoluted, it reutilises much of the previous implementation. The aforementioned product team proposes the following concept:
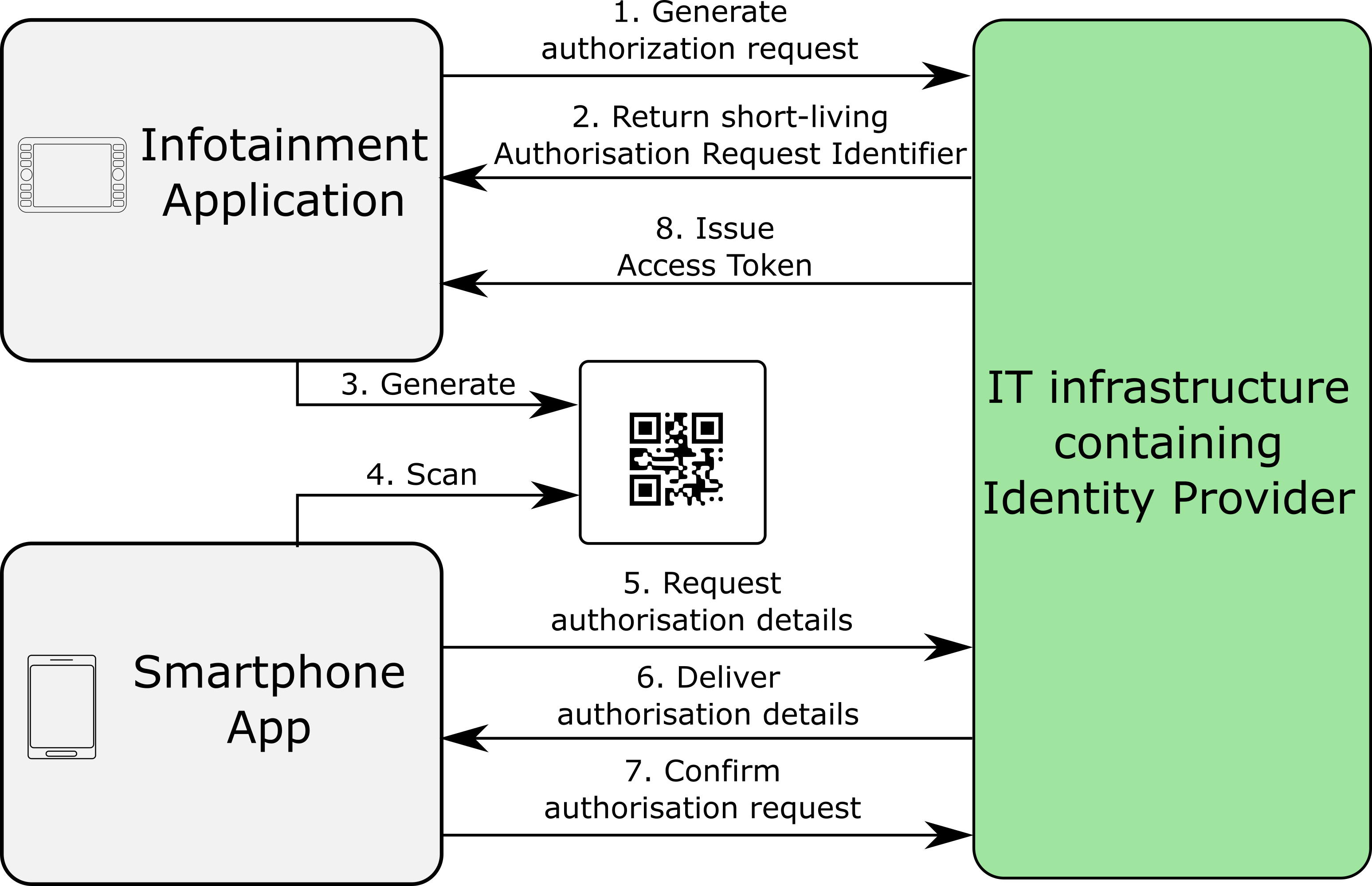
The infotainment screen will display a graphical code via the application. This graphical code contains an Authorisation Request Identifier (ARI) which is obtained by sending a request to the IdP, who generate a short-lived ARI in return. The same ARI is also displayed as an alternative.
The user scans the graphical code via their smartphone app after logging in. The user is already logged in. Finally, the user confirms the authorization requests.
The IdP issues an access token which the car's application can use to access all APIs.
If desired, the user can easily revoke this access within the app. However, access is automatically revoked as soon as the ignition is turned off.
This approach enhances usability without compromising security. The business owners are satisfied with this implementation and do not expect many complaints as the smartphone has become an everyday item.
Benefit, Enhancements and Summerising
The clear benefit lies in achieving an appropriate balance between user-friendly access and high security standards. This approach allows for potential improvements, such as employing authorisation for more precise control. One possible revision would be to limit some features of the in-car application or prohibit access to certain functionalities, such as not allowing access to payment information and account settings for API calls coming from applications deployed on the infotainment system. Additionally, revoking an access token (together with a refresh token) would offer the advantage of retaining a user's active sessions.
Implementing authorization requests can provide short-term access to a remote application. User-friendly graphical code scanning is a likely method, especially as a user can be assumed to be logged in with their smartphone at all times. When it comes to security, it's important that the authorisation request is implemented using state-of-the-art technology and algorithms. For this reason, you should consider using authorisation frameworks such as OAuth 2.0 to issue access tokens.